Third Party Firewall | installation GlassWIre
As I mention in previous entries, firewalls represent an essential layer of security in any environment, filtering the incoming and outgoing traffic. Back in time the built in firewalls were weak and most of the users and professionals concerned for their network's security used to rely on third party firewalls. Nowadays, the OS built in firewalls are more than capable to provide solid security measures and filtering configuration to protect a device.
But, there are cases where a third party firewall could be beneficial, like when a host connect directly to the internet, or when it is connected to a public networks. However is not really common, I will install and configure a firewall as a tutorial. The free version of GlassWire.
GlassWire is a good choice for its multiple features; graphics with network activities, letting you drill down into exactly which application is connected to where and how much bandwidth a application is using. It also makes network security checks like system file detection, device list change detection, app info change detection, and ARP spoofing monitoring. Making this firewall a full IDS.
installation / Configuration
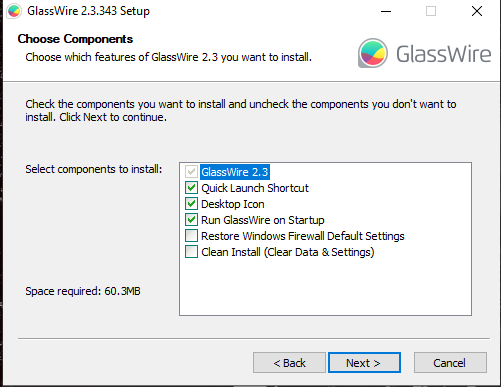
Once downloaded from the official website and accepting the terms and conditions. The best option of installation is to follow the preset installation settings.
Once installation is complete the firewall app will start with this interface, then you should move to the firewall toolbox and power it on.
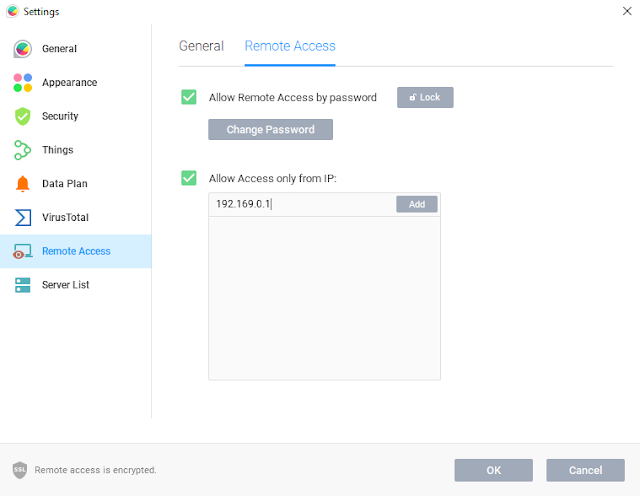
Then click on the top left and select settings, then remote access, once again remote access and unlock and click in remote access by password. It is important in this step configure a safe password, you can check this previous post to check how to create a bulletproof password.
Now it is time to add the IP addresses that you would like to add to your whitelist, in case that an user needs to set up one.
NOTE: It worth nothing to mention that in most of the cases IP whitelist are not really recommended as the could suppose a security threat. One of the main reason is because the IP addresses are logical and non permanent addresses. It would be just recommended in cases like a network administrator would like to Restrict the access to corporate resources such as cloud-hosted environment on platforms to a specific IP addresses



Comments
Post a Comment